At Amarula Solutions, we have built extensive experience in realizing IoT solutions. One of the technologies we like for its cost-effectiveness and multi-faceted use-cases is Near Field Communication (NFC) technology. With a deep understanding of NFC’s capabilities, we have successfully implemented NFC solutions that address the critical needs of our customers’ businesses.

Our expertise in NFC technology has led us to implement real-world use-cases, one of such applications, the brand protection solution, has especially proven to be popular due to its low cost, simplicity and effectiveness to help businesses protect their products and intellectual property from counterfeiting.
Amarula Solutions has collaborated with luxury brands, deploying NFC-enabled authentication solutions that verify the authenticity of high-end products. By ensuring customer confidence and preserving brand integrity, our solutions have helped protect luxury goods from counterfeit copies.
We deliver complete packages, the solution we have delivered to our client included:
- Proof of Concept: We conducted a case study on the cryptographic capabilities of NFC using NXP NTAG 424. Each tag is configured with a unique cryptographic key that cannot be extracted. This key is known only to the tag and the backend server and is used to authenticate the tag when tapped with an NFC-capable mobile phone. During the proof of concept, we tested two methods of authenticity verification: Secure Dynamic Messaging (SDM) and Standard Secure Messaging (SSM). The SDM method produces a Secure Unique NFC (SUN) message when the tag is read, which contains data, including a dynamic counter. This SUN message is sent to the server for verification. The server uses the correct cryptographic key to verify the message data and it also performs a check using the counter to ensure that the same SUN message is not used multiple times, to prevent replay attacks. However, one vulnerability of the SDM method is that the SUN messages could be read in advance from genuine NFC tags and later injected into counterfeit tags. The server can only verify the message itself, but cannot determine if it was produced in real-time by a genuine tag during verification. This creates a risk of counterfeit tags being authenticated as genuine. Due to this vulnerability of SDM, we concluded that SSM is more secure. As a result, we successfully implemented SSM with AES mutual authentication.
- Business Initialization Application: We developed a business application that allows companies (tag provider) to initialize NFC tags with securely generated unique keys. The application receives the keys from the server and injects them into the TAG. During the initialization process, the business application can send to the server additional meta-data which can be used for marketing and logistic purposes. The server will register the tag properly and associate it with the correct products.
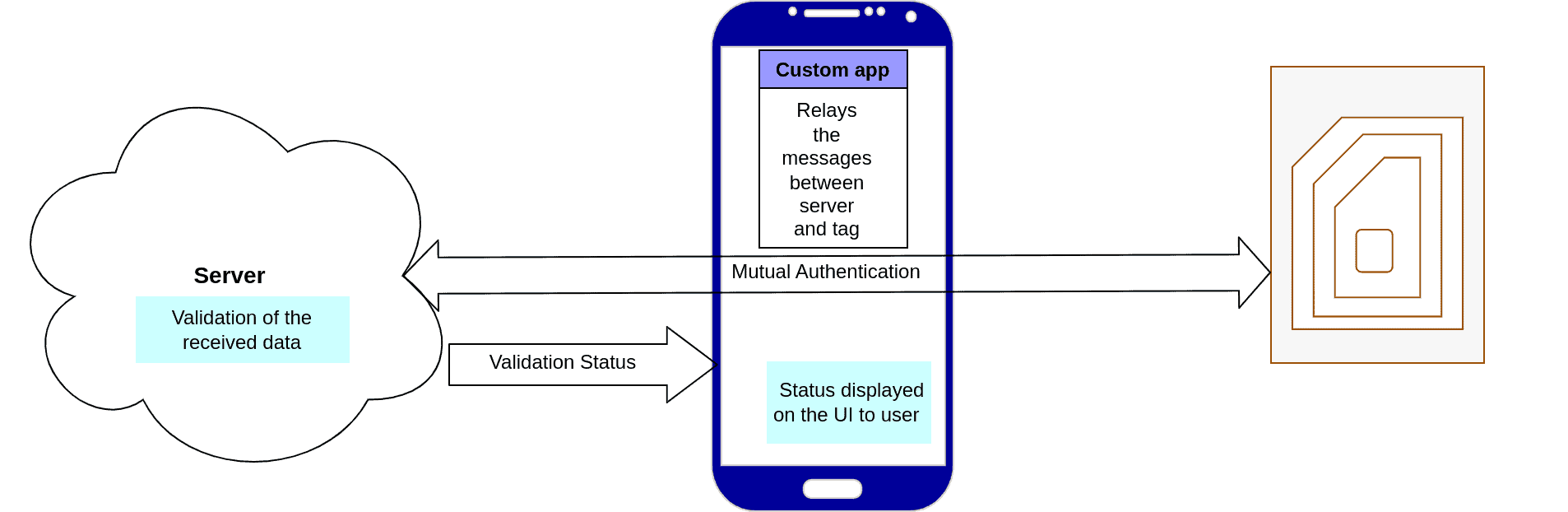
- User Validator Application: The user application serves as a router between the server and TAG to perform mutual authentication. It also serves as the interface to display the final verification result. Thanks to mutual authentication with AES symmetric keys, known only by the tag and server (using challenge and encryption from both sides), the server can ensure at runtime that it is communicating with a genuine tag at the moment of verification. Thus, the application enables users to verify the product’s authenticity and boost customer confidence. Additionally, the mobile application provides opportunities for interactive customer engagement beyond verification.
- Server Validator: The backend server is configured with the symmetric keys which are also injected into the tags. During the verification process a secure communication channel is established between the tag and the backend server. If the authentication is successful, the result is provided to the mobile application interface.
In addition to our implementation of the brand protection solution, we have explored various other use-cases that utilize NFC technology’s potential. These use-cases demonstrate the versatility of NFC beyond brand protection, showcasing its value in diverse domains. Some examples of use-cases that businesses find interesting are:
- Smart Retail Experiences: NFC tags integrated into retail displays and products offer interactive experiences, delivering product information, personalized offers, and enabling seamless mobile payments.
- Interactive Marketing Campaigns: NFC technology facilitates interactive marketing campaigns, allowing customers to engage with promotional materials, access exclusive content, and participate in contests or surveys.
- Secure Digital Content Distribution: NFC can be used to securely distribute digital content, such as music, videos, or e-books, by leveraging cryptographic authentication and authorization mechanisms.
- Supply Chain Support: By incorporating NFC tags into product packaging or shipping containers, businesses can support their processes in the supply chain, ensuring transparency, quality control, and detecting any tampering or unauthorized handling.
Amarula Solutions is dedicated to utilizing the full potential of technologies like NFC. In addition to our track record of implementing successful IoT applications, we conduct proof of concepts and feasibility studies to explore new use cases. We are committed to delivering innovative and secure solutions tailored to our clients’ specific needs. Whether you are seeking NFC technology for brand protection initiatives or exploring its potential in other applications, our team of skilled engineers is ready to assist you.
Contact us today to learn more about our NFC expertise and discuss how our services can contribute to the success of your business and help turn your NFC vision into reality. With our presence across Europe, we are well-positioned to support your projects and drive your business forward.